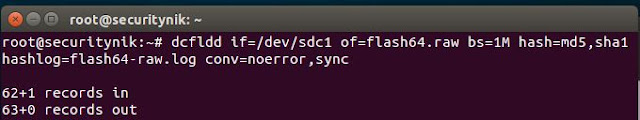
Next we verify that both the output file and the log files are created and below we see they are.
 Now let's use foremost to see if we can retrieve the same data as shown above.
Now let's use foremost to see if we can retrieve the same data as shown above.Before running any tool you may want to see what the help has to offer in terms of guidance.
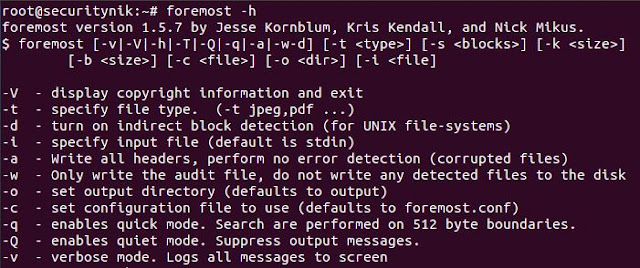
For foremost, we can execute "foremost -h" to get help as shown below.
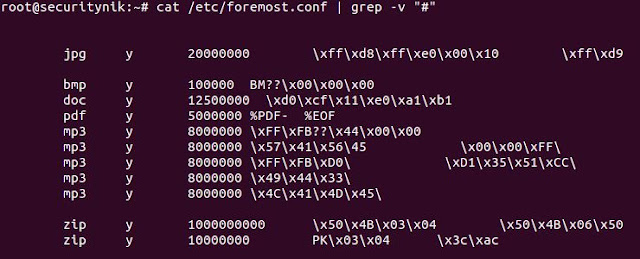
Next let's edit the foremost config file. "vi /etc/foremost.conf". I edited the default configuration file, allowing it to search for the file extensions which are on the drive. If the drive only had .pdf files I could have searched for just that. In this case I'm searching for pdf, bmp, doc, mp3 and zip. The objective was to not look for things which were not there. Additionally, it is important to understand how the "foremost.conf" file is structured as you may wish to add your own file structure to search for.
Next I create a temporary folder named "securitynikTmp" using "mkdir securitynikTmp"
Let's now run foremost to see what we get
root@securitynik:~# foremost -c /etc/foremost.conf -o securitynikTmp -v flash64.raw
- c: Tells foremost to use the configuration file which is found in "/etc/foremost.conf"
- o: Tells foremost to use output directory "securitynikTmp"
- v: Tells foremost to be verbose
flash64.raw is the file which will be used as input to foremost
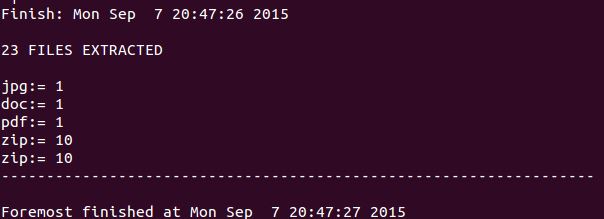
Once foremost has completed we see the following (note that the actual files extracted has been omitted for brevity).
Next if we perform a "ls" on the "securitynikTmp" folder, we see the following listing showing that foremost created a folder for each file extension type.
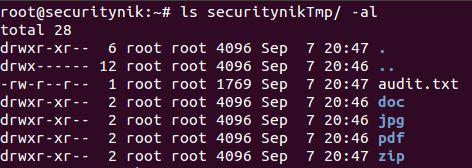
The "audit.txt" shows the output from the execution of the foremost command. Basically this information is much similar (if not the same) to the information which was seen on the screen during the execution of foremost.
Let's now look at the "pdf" folders. Below we see there was one pdf file.

Let's open this file using "xpdf" and see what the contents provide us.
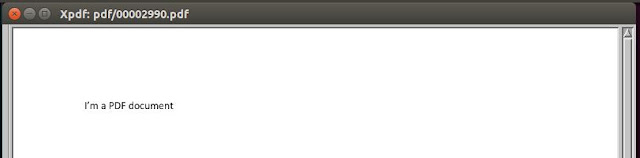
As we can see the pdf file opened successfully.
That's it for foremost. Next post we will use scalpel to perform the similar task.
References:
Foremost
xpdf
dcfldd

Sorry, I have not touched formost in a while.
ReplyDeleteNoted with thanks!
ReplyDelete